Overview
Microsoft has provided its customers with the ability to protect their sensitive files using its Encrypting File System (EFS). EFS allows for the transparent encryption and decryption of sensitive files and is billed as a solution to protect documents in the event of the physical compromise of a computer. This article will show that it is possible to forensically recover documents protected with EFS without resorting to breaking its encryption.
What is EFS?
EFS is an additional technology added to Microsoft’s New Technology File System (NTFS) beginning with Microsoft Windows 2000. It allows for the transparent encryption and decryption of protected files with minimal additional effort required by the end user.
Purpose
The purported purpose of EFS is to protect unauthorized access to protected files beyond the protection provided by the standard NTFS file permissions. This means that EFS should protect the document from unauthorized access even in the event that the system is compromised or stolen. The basic line of thinking is that even if you cannot stop unauthorized individuals from gaining access to the file itself; EFS will still protect the contents of the file.
How EFS works
EFS uses a hybrid of both symmetric and asymmetric encryption algorithms. A detailed look at the internals of EFS can be found here.
It is important to note, as the conclusion highlights, that to be able to access the encrypted files each user’s public/private key pair is stored on the local computer in the users profile directory.
What is digital forensic analysis?
Digital forensic analysis also known as computer forensic analysis is the process of examining digital media for evidence. Digital media can consist of:
- computer hard drives,
- cell phones,
- cdroms,
- floppy disks,
- USB thumb drives, etc.
Computers only do what they are told and the traces of their activity are left on the computer’s storage areas - cause and effect, actions and evidence. So, analysis of digital media provides evidence of an individual's actions, and when combined with evidence gathered in a large investigation, can show if and how someone lied, cheated or planned out an action. Those who try to hide their actions using encryption only end up showing they felt they had something to hide.
Test plan
So how effective is EFS at keeping protected files away from prying eyes? This test will only focus on how effective EFS is at hiding information. There will not be any attempt to break EFS - just work around it. All encryption can be broken; it’s just a matter of time.
The test plan will consist of:
- Create an unencrypted document that we will then encrypt.
- Create a document that should be immediately encrypted.
- Analyze the hard drive and find the encrypted files.
Create evidence
To make sure that no stray files can cloud the results; the test will include installing all the software to a computer.
Test computer
The test computer will consist of using a 10GB VMWare virtual computer. Microsoft Windows XP and Microsoft Office 2003 are the only software installed that will be installed.
Folder creation
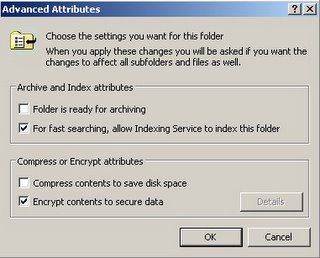
A single user account named "qwerty" will be created and used. The first step is to create a folder named EFS in My Documents.
Next, create two sub folders “encrypted” and “unencrypted”.
Enable EFS on the “encrypted” folder.
File creation
First, create a new word document in the “unencrypted” folder.
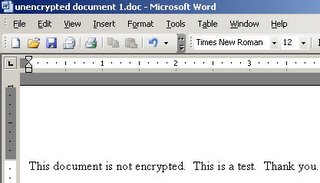
Then, add some text to the document.
Repeat the file creation steps in the "encrypted" folder.
Digital forensic analysis
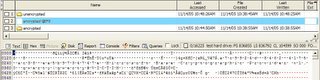
Now that the evidence is created analyze of the hard drive can begin. The first evidence discovered is the alternate data stream $EFS connected to the “encrypted” folder. Note that the bottom of the screenshot shows the content of the alternate data stream. It contains the symmetric key used to encrypt the files that is itself encrypted with the default user account’s (“qwerty@victim”) public key. This can be taken and “cracked” offline.
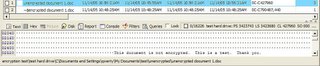
Next the “unencrypted” folder is reviewed. Note the “~$encrypted document1.doc” file. This is the temporary file that Microsoft Word creates when a document is edited. The content of the file is visible at the bottom of the screenshot.
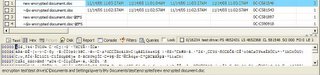
Looking at the “encrypted” folder show the existence of two alternate data streams, each belonging to a word document, note the difference in the bottom of the screenshot where the encrypted document contents are visible but unreadable.
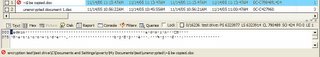
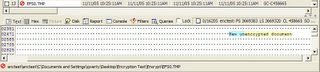
The problem for EFS is when documents move between encrypted and unencrypted areas of a hard drive. The screenshot below shows the result of a file move below. When a file is moved the original location is deleted - but not overwritten - allowing for the recovery of the unencrypted version. Not shown is the fact that portions of protected documents end up in the pagefile in unencrypted form.When EFS first encryptes a document, it copies the unencrypted contents to a file called "efs0.tmp" in the current folder. The data is then encrypted, written back to the original file, and then the temp file is deleted. This exposes the last endited file in each folder in a potentialy recoverable state as the screenshot below shows.
Findings
Temporary file issue
Temporary files are deleted but not overwritten allowing for clear text versions of encrypted documents to be found and recovered.
File names
All the file names of documents are left unencrypted. This is by design, however, this allows attackers to focus attentions on files that are named after what an attacker wants such as “2005 banking information.doc”
Key recovery
While beyond the scope of this test; the fact that the encryption keys are on the system allows for the keys to be stolen and broken.
The user problem
Notice that no additional steps were required for a user to use encryption other then selecting a folder to encrypt? Any access by the user allows for the transparent decryption of the files. This reduces the security of EFS to the user’s password.
Conclusion
It is unfortunate that current security follows the sliding scale from hard to use but secure to easy to use but insecure. Microsoft designed EFS to be easy for the average user to use. In so doing, it fails to meet the purpose of encryption – protecting documents from physical access to the computer or digital media. The fact that encryption will be inconsistently applied to user data and the fact that deleted files are not viewable by the end user allows for unencrypted data to remain on the system. The encryption keys also are stored locally putting the encrypted data at risk. The final failing for Microsoft is not recognizing that over 90% of users will disclose there passwords when asked. Social engineering is still the biggest vulnerability to your data – because there is no patch for human stupidity.


No comments:
Post a Comment