I was talking with a friend the other day about how malware uses email to hack into computers. What’s malware? Read my previous article: Adware and Spyware – are they really consensual? Anyway, my friend responds back that he uses Hotmail to protect his identity and to avoid malware. Instead of getting into Internet Explorer or Microsoft bashing, I instead chose to focus on his comment of protecting his identity. Used properly, a web email address is great as a spam trap for all the products and web sites that require an email address to register. Create a fictitious web email address and use that as the spam catcher saving your “real” email address for friends and family. Unfortunately, my friend believed that a web email address couldn’t be traced back if used at work or other public computer such as a coffee shop kiosk. I plan to show both my friend and you just how exposed your private emails are.
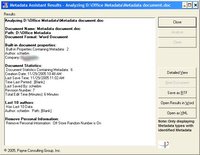
A forensic analysis of a computer shows everything that exists on the hard drive – files, folders, deleted text and images, etc. The truth is that nothing is ever really deleted only eventually overwritten. The dirty joke you deleted last month can come back to embarrass you tomorrow. Let’s do a hypothetical forensic analysis of a computer where someone accessed a hotmail email account using Internet Explorer.
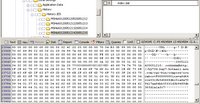
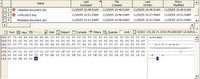
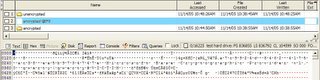
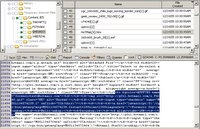
Internet explorer tracks the web actvity of each user in a file named index.dat. If you look at the text in the bottom right panel you will see hotmail.msn.com. Now that we know this user uses hotmail its time to see if there are any old messages to discover.
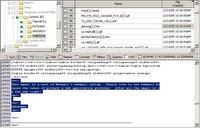
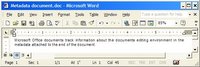
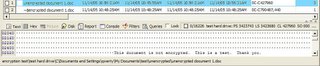
All hotmail emails opened on a system create a file named getmsg[#].htm, where the '#' is an incremented number. So a quick scan for getmsg*.htm finds the first email message. If only we could clean up this ugly html and see the email the same way the user did ...
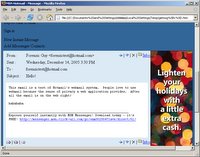
That’s much better. Hmm I wonder what other messages were in his inbox ...
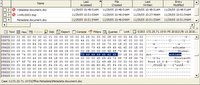
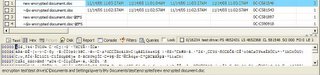
Similar to the getmsg*.htm files, all hotmail inbox web pages are named hotmail[#].htm. A simple search for hotmail*.htm finds another ugly html page. Let’s clean it up a bit.
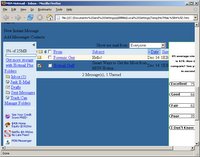
Now we have his entire inbox in all its glory along with all the people who emailed him. I wonder what a search for those names would turn up. Well, maybe some other time. This is just a sample of how exposed web email is to discovery on any system you use to access your email. But wait, there's more! The emails fly across the Internet for all to see. Now I cheated and sniffed the email as it went across the Internet using a tool called Ethereal, which is available for anyone to download and use.

Ethereal is a good example of a protocol analyzer and one of my favorites. It is an open and free to use product with a good community support network that maintains a valuable User’s Guide online.
Getting back to our hypothetical analysis; let’s look at what we captured.
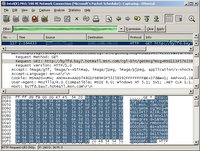
This is what anyone on the Internet *could* see – your coworker in the next office, the weird dude next to you in the coffee shop, anyone. Yes, you probably have to be a geek to understand what this stuff means, however, Ethereal has a feature near and dear to my heart. It’s called “follow TCP stream” that reassembles the network packets into something a human can read.
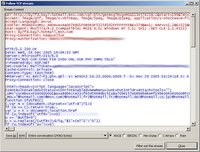
Ok maybe not that screenshot but how about we scroll down some ...
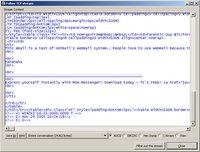
Hey look there is that all so secure and untraceable webmail message! Hmm, I guess my friends and family won’t ever let me borrow their computers again – darn. Now imagine you're in some coffee shop or airport with your wireless Internet connection chatting away and reading your email. Now look over and see the fella just staring at his screen – he looks up and makes eye contact and smiles. Now imagine the above screen shots are on his computer and that’s your email making him smile.
Now I hear you, “I empty my Internet cache! That protects me right?” Wrong.
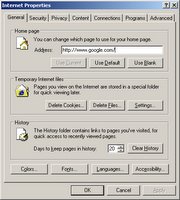
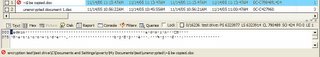
Clearing history …. Deleting files ...
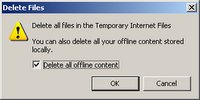
All those files ...
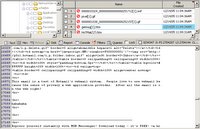
And I can still find them. See the nice red symbol in front of the file name? That means its “deleted”. Remember: Nothing is deleted on a computer - only overwritten. If you're using Microsoft Windows XP then you have some help from a tool called cipher.exe.
What cipher.exe can do, beyond encrypting your files (see my article Microsoft Encrypted File System – Digital forensic analysis) is to wipe or overwrite all the deleted files on the computer.
After a long while the content of all those deleted emails will be purged and non recoverable.
So is webmail more secure or untraceable that normal email? Depends on what you use it for. If you’re using a fake account to trap spam; the answer is yes. Are you using webmail because it’s available from anywhere? Well, let’s just hope that I’ve scared you off a little. Well till next time - see you at the coffee shop!